Master Solutions Blog
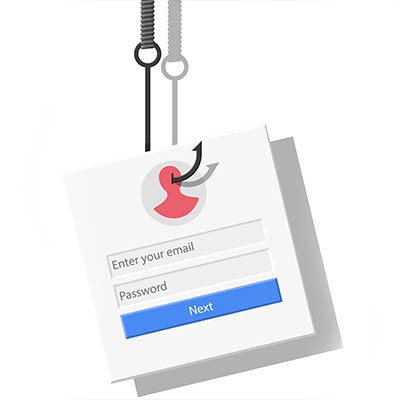
Unfortunately, not every message that lands in your inbox has your best interests at heart. Malicious actors are casting wider and more sophisticated nets than ever before, hoping to reel in an unsuspecting employee and gain access to your business' valuable data and finances. Fear not, with a little knowledge and a healthy dose of skepticism, you can learn to spot these email scams and keep your organization safe.
Backup is a decidedly unsexy topic to discuss, but it’s important nonetheless. You can’t trust that your files will always be there—not unless you take action to ensure they’re well-protected and preserved for when you need them most. While you’re busy with other parts of running your business, you need to know with certainty that your files are safe, and we can offer that.
Presentation anxiety is very real and can present itself in various ways, from dry mouth to sweaty palms to a sudden loss for words. It’s a legitimate phobia that people have, which makes it all the more helpful that modern presentation tools offer a feature to help mitigate its impact: Presenter View.
Let’s talk about how to put Presenter View to use in either Microsoft PowerPoint or Google Slides.
Today is Global Wellness Day. As such, we wanted to invite you to consider a few ways to prioritize not just your mental and physical well-being, but your digital well-being as well. After all, technology is what keeps us connected to the world at large… and if we don’t approach it appropriately, it can create some challenges that we should all want to avoid.
Let’s talk about some simple best practices that can help promote workplace wellness and a healthier balance in our lives.
A data breach—when a company’s sensitive data, from customer details to company secrets to financial information, is exposed—certainly isn’t a good thing for any business to experience. Once an organization knows it’s happening, it’s time to go into panic mode.
While this is an understandable response, it is crucial that you are prepared with a strategy to navigate such a situation should it ever arise.
Let's be honest, technology can sometimes cause big headaches for businesses. Maybe your main computer system crashed right when you were busiest, or you had a scary data problem. These tech troubles can frustrate you and your customers.
Remember Y2K, around the turn of the millennium? It was a time when everyone worried that all computers would crash. The whole thing actually made many companies upgrade their tech and get better prepared. The lesson is that even big technology problems can lead to good changes.
What are your plans for the summer? If they involve getting out of the office and going on a vacation, then you’ll want to be armed with a couple of technology tips to help you make the most of your time in a safe and secure environment. Here are three tips you should keep in mind this summer.
If you are like most people, you are probably juggling a million things at work, and when an email pops up from your boss, your instinct is to take it seriously. Hackers know this, and they're getting good at creating fake emails that look exactly like they're from your manager to get you to make a mistake and give them what they need to access your digital accounts and the data that lies therein.
More often than not, you have an employee on staff who rolls their eyes whenever you have to send out another cybersecurity email or reminder. This “who cares” mindset is dangerous and can infect your business in a profoundly disturbing way. Today, we want to get into why this “who cares” mindset is so dangerous and what’s really at stake when you have an employee who can’t get on board with your security policies.
While the goal of cybersecurity is always to prevent threats from taking advantage of your infrastructure, this is becoming more and more challenging as time wears on and threats evolve to changes in cybersecurity discourse. A recent podcast episode from Illumio, “Trust & Resilience: The New Frontlines of Cybersecurity,” explores how trust has become a vulnerability that attackers exploit in new and creative ways. How can cybersecurity as an industry pivot in response to this trend?
Modern cybersecurity requires you to lock down numerous access points to protect your business, using various tools to accomplish sufficient security precautions. The password manager is one such tool that can genuinely save your metaphorical bacon.
Let’s explore how this essential tool works and why it is valuable for your business to implement.
Imagine for a moment a world where you don’t have to distribute devices to your employees and can instead rely on your team to provide them. With Bring Your Own Device, or BYOD, businesses can leverage employee-owned devices to their advantage for work-related purposes. There is a catch, though: you have to make sure they’re used safely.
For businesses, staying compliant with data regulations isn’t just about avoiding hefty fines; it’s about building trust with customers, protecting sensitive information, and keeping operations running smoothly. Ignoring compliance isn’t an option. A single slip-up can lead to legal trouble, financial losses, and serious damage to your company’s reputation.
Your Internet browser is probably one of your most used apps. For this reason, it is important to know how to effectively use it. Regardless of what browser you use, you need to understand how to use these four very useful features. Let’s dig in.
Running a small business sometimes feels like a never-ending juggling act. One minute, you're answering emails, the next, you're dealing with customer requests, and before you know it, the day's over, and your to-do list is somehow longer than when you started. The good news is that you don’t need to clone yourself to make your business work. You just need a disciplined plan to manage your time.
Multitasking might commonly be seen as a super skill that all employees and business professionals should master, but is it really all it’s cracked up to be? The truth of the matter is that multitasking doesn’t work, even if it looks like it does. In fact, all it succeeds in doing is making you work slower while increasing your stress and decreasing productivity.
The new year brings exciting opportunities—but unfortunately, it also brings new chances for hackers and cybercriminals to cause trouble. That’s why it’s so important to stay alert and prepared for the cybersecurity threats we might face in 2025.
It’s harder than ever to keep your data safe these days. Everyone needs to be careful online, but the constant security steps can feel exhausting when you’re spending hours on a computer every week. Unfortunately, this is the new normal. If you don’t stay on top of your cybersecurity, it can be really hard to keep your business’ tech safe.
Most people are familiar with Santa Claus, the jolly gift-giver who delivers presents to all the children who have kept the Christmas spirit in their hearts all year. Lately, many people have also become aware of Krampus, Santa’s dark shadow who—as the legend goes—takes a similar trip to visit the naughty children and turn the worst into a midnight snack.
However, one has to wonder: what about all the adults who might also be naughty?
Passwords open all of your online accounts, so creating one that’s both strong and easy to remember is extremely important. A lot of times, it can be an issue; which is why one of the most common IT-related problems our help desk remediates is lost password credentials. Let’s take a look at what makes a secure password and how to effectively do it.